
Hurdles on the internet are a common happening in everyday life. Whether it is a small non-profit organisation or a large MNC, platforms face security threats and traffic menace on a daily basis. It is unsure that the email, website, anything that face the internet is safe. One of the insecurities that organisations undergo is Distributed Denial of Service (DDoS) attacks.
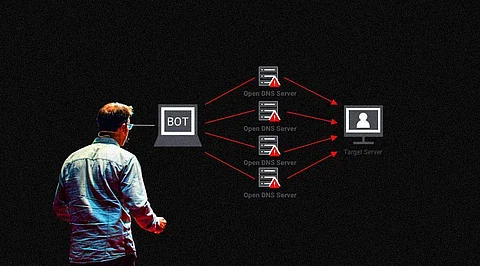
A distributed denial of service (DDoS) attack is one of the most powerful weapons of the internet. The DDoS attack means that the hackers have attempted to make a website or computer unavailable by flooding or crashing the website with too much traffic. The main target could be a wide variety of important resources like banks or news websites.
However, sometimes DDoS attacks take place to distract the organisation from the underway cybersecurity attack like criminal activities or data theft. The statistics behind a DDoS attack is simple. A server, service, site, website, or a network is flooded with internet traffic making it inoperable. The device used to accomplish the task is a network of remotely controlled hacked computers or bots. These devices are referred to as 'zombie computers.' The hacked computers form a 'botnet' or network of bots which is used for trafficking.
The botnets send connection requests to a server more than it can handle making it go berserk and inoperable. It might also send an overwhelming amount of data that exceed the bandwidth capabilities of the targeted victims. Cybercriminals control the botnets with thousands of hacked computers. Other than trafficking, cybercriminals also use botnets to send spam or forms of malware such as ransomware. There are chances that any computer without the knowledge of the owner could be a part of botnet.
A DDoS attack of one gigabit per second is enough to knock most organisations off the internet. But recent attacks are on the count of terabits generated by hundreds of thousands or even millions of suborned devices. DDoS attacks fall under some general categories. Some of them are even sophisticated attacks combining attacks on different vectors.
Panix, one of the oldest internet service providers was the first victim of DDoS attack that took place in 1996. The server was knocked offline for several days by an SYN flood, a technique that has become a classic DDoS attack. Later in 2000, Michael Calce, a 15-year-old bot with an online name 'Mafiaboy,' launched a severe DDoS attack. The servers that crashed during the attack includes CNN, E-Trade, eBay and Yahoo. Over the next few years, DDoS attacks became common. Cisco predicts that the total number of DDoS attacks will double from the 7.9 million seen in 208 to over 15 million in 2023. The covid-19 that has pushed companies to function on remote working has maximised the opportunities for such DDoS attacks.
A gigantic DDoS attack took place in February 2020 crippling Amazon Web Services. The attack used a technique called Connectionless Lightweight Directory Access Protocol (CLDAP) Reflection to target an enormous number of AWS customers. The technique amplifies the amount of data sent to the victim's IP address by 56 to 70 times with vulnerable third-party CLDAP servers. The attack lasted for three days making AWS lose revenue. The brand also suffered severe damage.
The previous largest attack happened in 2016 to the blog security expert Brian Krebs. Krebs had recorded 269 DDoS attacks since July 2012, but this attack was three times bigger than all its previous crashing.
Mirai botnet, a DDOS attack system that came to light in August month of the same year was behind that attack. Mirai botnet consisted of more than 600,000 compromised Internet of Things (IoT) devices such as IP cameras, home routers and video players.
Next big attack was in September that targeted one of the largest European hosting providers, OVH. The provider holds around 18 million applications for over one million clients. The attack lasted for 7 days crippling the system by a generated traffic load of 1.1 terabits per second. Mirai made a name mark to the DDoS attack. It showed the world how powerful a DDOS attack could be with the scale and focus of the attacks.
On September 30, it was allegedly claimed that the author of Mirai software released the source code on various hackers forum following the replication and mutation of the source. But still, in October 2016, Dyn, a major Domain Name Service (DNS) provider was flooded with one terabit per second of traffic that set a new record on DDoS attack. The disaster knocked Dyn's offline rendering a number of high-profile website including GitHub, HBO, Twitter, Reddit, PayPal, Netflix and Airbnb.
The Mirai's code release enabled anyone with modest information technology skills to create a botnet and mount a DDoS attack without much effort.
One of the earliest but severe attacks on DDoS was the targeting on six US banks in March 2012. Bank of America, JPMorgan Chase, U.S. Bank, Citigroup, Wells Fargo and PNC bank got their servers hijacked from a botnet called Brobot. Brobot generated 60 gigabits of DDoS attack traffic per second.
It was alleged that Izz ad-Din al-Qassam Brigades, the military wing of the Palestinian Hamas Organisation carried out the attack.
The most recent large scale DDoS attack was on GitHub, a software developer. The platform faced 1.35 terabits per second of data that lasted 20 minutes in February 2018. The reason or the attacker behind the scene is unclear. But it is said that the attack was created by over a thousand autonomous systems (ASNs) across tens of thousands of unique endpoints.
Protecting the system from becoming a botnet or stopping a DDoS attack is a tough job. However, it doesn't mean the task is impossible. If companies have a plan to defend and mitigate such attacks using the vulnerability of essential elements of any protection protocol will help.
Join our WhatsApp Channel to get the latest news, exclusives and videos on WhatsApp
_____________
Disclaimer: Analytics Insight does not provide financial advice or guidance. Also note that the cryptocurrencies mentioned/listed on the website could potentially be scams, i.e. designed to induce you to invest financial resources that may be lost forever and not be recoverable once investments are made. You are responsible for conducting your own research (DYOR) before making any investments. Read more here.
